EU cybersecurity directive NIS2.0 – What it is and how you should act?
NIS2.0 – The new EU-wide cybersecurity directive is coming in 2024. In this blog post we’ll tell you what it is, why and how you should act, and what are Microsoft’s Solutions for NIS2 Compliance. Deadline for this is October 17th, 2024.
Want to hear more how to implement the requirements of NIS2 in practice? Order our free webinar recording in finnish!
What does NIS2 mean for me?
Two main areas where NIS2 takes affect are:
- Cybersecurity Risk Management Measures
- Incident Reporting Obligations
Source: Microsoft Security
Summary for the C-level management
NIS2.0 is the new EU directive on network and information security that aims to improve the resilience and preparedness of critical sectors and essential services against cyber threats. It will enter into force in October 2024 and will apply to organizations with more than 250 people. NIS2 applies to an organisation either:
a) directly if your organization operates in a field defined in the directive, or
b) if your client is an organization that operates in a field where NIS2 applies. Supply chain security, including security aspects of the relationship between each operator and its direct suppliers or service providers, is included in the directive.
NIS2-directive will require organizations to comply with a set of standards and obligations, such as reporting incidents, conducting risk assessments, implementing security measures, and cooperating with national authorities.
If you work in C-level management, you need to be aware of the implications of NIS2.0 for your organization and your customers. You need to ensure that your IT systems, processes, and staff are aligned with the new requirements and that you have a clear strategy and action plan to achieve compliance. You also need to communicate with your customers about the benefits of NIS2.0 and how it will enhance their security and trust in your services.
NIS2 will have a significant impact on business operations, reputation, and competitiveness. NIS2 will require companies to invest more in cybersecurity, comply with new rules and standards, and cooperate with national authorities and other stakeholders.
Failure to do so could result in fines of up to 10% of annual turnover, as well as reputational damage and loss of customer trust. On the other hand, complying with NIS2 can also bring benefits, such as improved resilience, innovation, and market opportunities.
NIS2 is not only a challenge, but also an opportunity for C-level management to demonstrate their leadership and commitment to cybersecurity.
Sulava offers services for the configuration and implementation of compliance and security as well as security audits, learning services and governance models. We support your organization in the deployment of the security services and functionalities. Read more at the end of the blog
More in detail: What NIS2.0 is and what are the key changes?
Let’s get to know the topic deeper. NIS2 is the new European cybersecurity directive that will replace the existing NIS1 Directive in October 2024. NIS2 expands the scope of the previous NIS1 Directive.
NIS2 is the most comprehensive EU cybersecurity legislation to date, covering 15 sectors including new sectors such as manufacturing and research. It includes medium-sized companies that are identified as critical infrastructure.
Who?
| Essential sectors: | Important sectors: |
|---|---|
| Energy | Postal and courier services |
| Transport | Waste management |
| Banking | Chemicals |
| Financial market infrastructure | Food |
| Health sector | Manufacturing of medical devices |
| Drinking water | Digital providers |
| Wastewater | Research organizations |
| Digital Infrastructure | |
| IT service management | |
| Public administration | |
| Space |
Directives purpose is to establish a baseline of minimum-security measures for digital service providers and operators of essential services, to mitigate the risk of cyber attacks and to improve the overall level of cybersecurity in the EU.
Key Changes from NIS1 Directive to NIS2
• NIS2 sets out a benchmark of minimum measures:
That companies need to take actions to improve their cybersecurity posture. These include conducting risk assessments, implementing multi-factor authentication, and having plans for incident response and supply chain security.
• NIS2 introduces stricter enforcement:
Through enhanced measures and sanctions for non-compliance with the directive, as well as more stringent supervisory measures for national authorities.
• NIS2 establishes a framework for coordinated vulnerability disclosure
and creates an EU registry for vulnerabilities, operated by ENISA, The European Union Agency for Cybersecurity.
• NIS2 also enhances cooperation and information sharing between Member States and their authorities, including on cyber crisis management.
To comply with NIS2, you will need to take the following steps:
- Identify your role and obligations under the NIS2 Directive. Depending your role, you will have different responsibilities and requirements to meet.
2. Assess your current level of cybersecurity and identify any gaps or weaknesses. You will need to follow common standards and guidelines for security and resilience that will be developed by ENISA and the European Commission.
3. Implement appropriate security measures and policies to protect your systems and data from cyber threats. You will need to adopt a risk-based approach and ensure that your security measures are proportionate to the level of risk you face.
4. Report any significant or major incidents to your national authorities and ENISA. You will need to follow a harmonized framework for incident notification that will specify the thresholds, formats and procedures for reporting.
5. Cooperate with your national authorities and other stakeholders. You will need to participate in regular audits and inspections by your national authorities and share information and best practices with other actors in your sector or across sectors.
More information about Cybersecurity Risk Management measures and Incident reporting

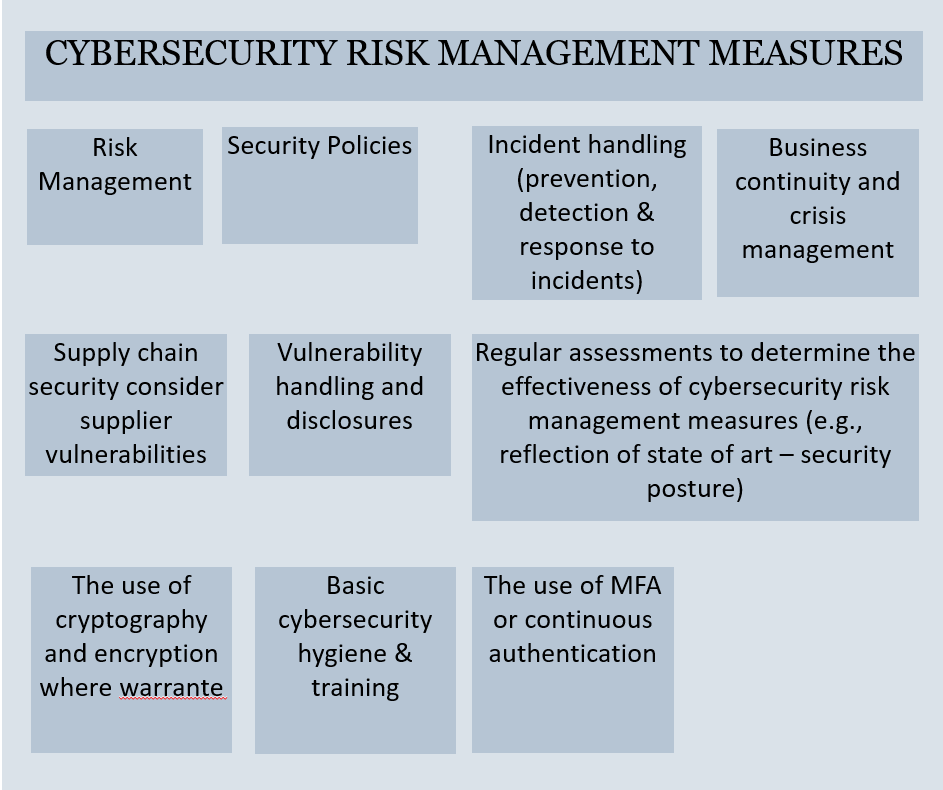
Cybersecurity Risk Management Measures
NIS 2 employs a risk-based, outcome-focused approach to measures addressing:
- risk analysis & information system security policies;
- incident handling;
- business continuity and crisis management;
- supply chain security;
- security in network and information system acquisition, development, and maintenance, including vulnerability handling and disclosure;
- policies and procedures to assess the efficacy of cybersecurity risk management measures;
- basic cybersecurity hygiene and training;
- policies and procedures regarding cryptography and encryption;
- HR security, including access control policies and asset management; and
- the use of MFA or continuous authentication solutions (Zero Trust) and other technical controls.

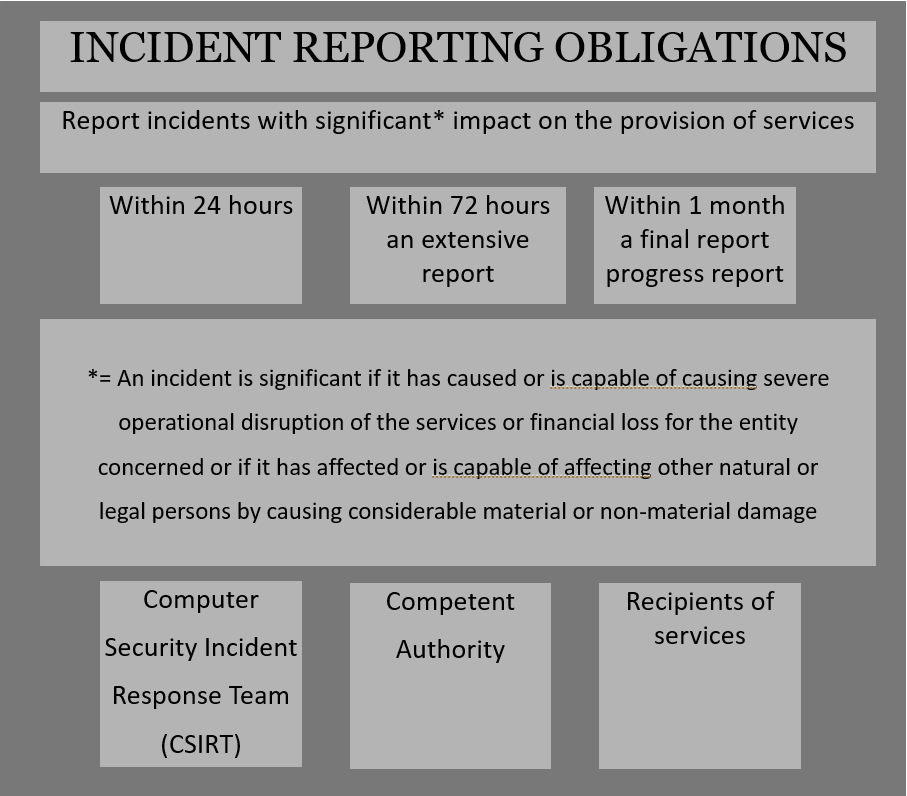
Incident Reporting
Report “incidents having a significant impact on the provision of their services” = causing severe operational disruption of the service or financial losses ; affecting other persons by causing considerable material or non-material losses.
- within 24 hours submit to the relevant authority an “early warning”
- without delay submit mitigation and prevention information.
- within 72 hours submit an “incident notification” (assessment, severity, indicators of compromise)
- upon request from the regulating agency submit interim reports
- within one month of initial awareness it will be required to submit either a final report or a progress report followed by further monthly progress reports until a final report.
Microsoft’s Solutions for NIS2 Compliance
Risk assessments:
Use Microsoft 365 Compliance Manager and Microsoft Defender for Cloud to assess risks and comply with regulations. Microsoft 365 Compliance Manager already provides assessment templates with detailed recommendations for NIS1. NIS2 assessment templates will be provided soon.
Use of cryptography:
Leverage Microsoft Azure Key Vault and Microsoft Defender for Cloud for secure key management and encryption.
Security around the procurement of systems:
Utilize Microsoft Intune and Endpoint Manager to manage devices and ensure security controls are in place.
Security procedures for employees:
With access to sensitive or important data: Implement identity and access management solutions such as Entra ID (previously Azure Active Directory) and Privileged Identity Management to control access to sensitive data.
Microsoft Information Protection including Data Loss Prevention can help to protect data and restrict how it can be used. In addition, Microsoft Insider Risk Management can help to detect and follow up on risky behavior of insiders.
Multi factor authentication:
Use Entra ID Multi Factor Authentication to add an extra layer of security to user sign-ins.
Policies and procedures:
For evaluating the effectiveness of security measures: The Microsoft Defender suite and Microsoft Sentinel can help you monitor and detect security threats in real time.
Plan for handling security incidents:
Microsoft Information Protection including Data Loss Prevention and Microsoft Insider Risk Management provide their own alert and incident management views.
Cybersecurity training and a practice for basic computer hygiene:
Utilize Microsoft 365 Learning Pathways and Microsoft Defender for Office 365 to educate your employees on cybersecurity best practices.
We can of course help you! To ensure the security and compliance know-how of both your IT-personnel and end-users, Sulava offers a wide range of training opportunities. We offer a wide range of courses in english and in finnish, both Microsoft official courses and our own. Contact us with your needs!
Plan for managing business operations during and after a security incident:
Use Microsoft Azure Site Recovery and Backup to ensure business continuity in the event of a security incident.
Security around supply chains and the relationship between the company and direct supplier:
Use Microsoft Defender for Endpoint to secure your devices and network against supply chain attacks.
Sulava offers services for the configuration and implementation of compliance and security as well as security audits, learning services and governance models. We support your organization in the deployment of the security services and functionalities. Read more at the end of the blog
NIS2 objectives and Microsoft Technology
| NIS Principles | Microsoft Solution |
|---|---|
| Governance | Defender CSPM, Entra |
| Risk Management | Defender XDR and Purview Compl. Mgr. & Insider Risk |
| Asset Management | Defender CSPM, Defender for Endpoint |
| Supply Chain | Defender XDR, Entra and DevOps |
| Service Protection | Defender for API |
| Identity & Access | Entra |
| Data Security | Purview |
| System Security | Defender for Endpoint, Defender for loT and Intune |
| Resilient Networks | Azure Network Security |
| Staff Awareness | O365 Phishing Simulation and Learning Paths |
| Security Monitoring | Microsoft Sentinel |
| Proactive Security | Defender XDR |
| Response and Recovery | Defender XDR, Azure Backup and Recovery |
| Lessons Learned | N/A |
Webinar about NIS2
Did you think NIS2 directive doesn’t apply to you? Join Sulavas webinar and learn 10 minimum requirements and practical advice! Order a free webinar recording that was held in finnish on the 8th of May 2024!
How to implement the requirements of NIS2 in practice? In this free webinar, you’ll get an in-depth overview of the EU directive aimed high level of data security from 2024 onwards. Sulavas experts Marko Mikkola and Oliver Lahti unravel the complexities of NIS2 and offer concrete measures and best practices to meet the requirements. Learn how to strengthen your organization’s ability to respond to security challenges and protect your organization from cyber threats.
Need help?
Take advantage of our help and expertise for security, compliance and training your personnel!
To help you to meet the requirements set by the NIS2 directive, we offer assistance with SOC & CSIRT monitoring services, assessing the maturity level of your cybersecurity capabilities, implementing and developing SIEM solutions, and supporting your organization in various administrative security tasks.
Read more about our security services, get in touch with us and start leveraging the security of the cloud in your environment!
Useful Links
NIS Regulations: Cyber Assessment Framework (itgovernance.co.uk)
In finnish: Finnish government proposal to implement the European Union’s Cybersecurity Directive (NIS2 Directive)
Microsoft video: What is NIS2.0 and how to prepare your organization and customers for it
Writers: Jussi Metso and Tatu Seppälä