Safeguarding Your Email: The Importance of DMARC and Exchange Online for your organization security
Email remains a primary target for cyberattacks, so monitoring your mail domain’s reputation and enforcing strong security settings is essential.
In this blog, we explore why strong policies are essential, the continuous monitoring and improvement of email reputation, user training, and emerging trends in email security.
We specifically delve into two critical aspects of email security: implementing DMARC to protect your domain (domain/email domain = the part after the @ symbol in an email address, e.g., sulava.com) from spoofing and leveraging Exchange Online security features to secure your organization’s email without hindering business operations. Additionally, we examine the use of the Microsoft Secure Score tool.
Common Email Threats and Why Strong Policies Matter
Every organization that uses email faces a variety of threats. Phishing attacks, where attackers send emails pretending to be trustworthy sources to steal credentials or money, are rampant. Spear phishing and Business Email Compromise (BEC) are more targeted forms that impersonate executives or partners to trick employees, often leading to large financial frauds. Malware and ransomware can arrive via email attachments or malicious links, encrypting data or stealing information.
A misconfigured or lax email security posture could allow these attacks through, with potentially dire consequences. Thus, having properly configured threat policies and up-to-date defenses is essential to intercept phishing emails, block malware, and prevent email impersonation before they reach inboxes.
DMARC: Protecting Domain Reputation and Preventing Spoofing
Domain-based Message Authentication, Reporting & Conformance (DMARC) is a protocol that helps ensure only authorized senders can use your domain, blocking impersonation and phishing attempts.
DMARC builds on SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to verify that emails appearing to come from your domain are actually sent by you. By publishing a DMARC policy in DNS, domain owners can instruct receiving mail servers how to handle messages that fail authentication checks. This is crucial in preventing attackers from spoofing your email domain for spam or fraud.
When properly implemented, DMARC stops unauthorized use of your domain, protecting your customers and partners from phishing emails that pretend to be from your company
Benefits of Implementing DMARC
Implementing DMARC offers several key benefits for organizations:
- Prevents domain spoofing and impersonation: DMARC stops unauthorized senders from using your domain to send malicious emails, ensuring that only legitimate emails get delivered. This protects your brand and recipients from phishing, spoofing, and business email compromise attempts.
- Protects brand reputation and trust: By blocking fraudulent emails from your domain, DMARC helps maintain trust with customers and partners, safeguarding your brand’s reputation. Recipients can trust that emails from your domain are authentic.
- Improves email deliverability: With DMARC, legitimate emails are less likely to be misclassified as spam by recipient servers. This means your real messages have a better chance of reaching the inbox, since email providers see that your domain has strong authentication in place.
- Provides visibility via reports: DMARC’s reporting feature gives domain owners valuable insight into how their domain is being used. Aggregate reports allow you to see who is sending email on behalf of your domain and whether those messages pass SPF/DKIM checks. These reports help identify unauthorized senders or configuration problems, so you can take action to fix issues and continuously monitor your email ecosystem.
Strengthening Exchange Online Security Settings
Microsoft Exchange Online (part of Microsoft 365) includes a suite of security features and policies that protect email on multiple fronts, and configuring these correctly is crucial to defending against threats.
Malware and ransomware can arrive via email attachments or malicious links, encrypting data or stealing information. Exchange Online’s security features are designed to mitigate these threats by filtering out suspicious content and enforcing authentication.
Exchange Online Protection (EOP), which comes with Exchange Online, provides built-in filtering against spam, malware, phishing, and other email-borne threats. On top of EOP, Microsoft Defender for Office 365 adds advanced features like Safe Links and Safe Attachments for enhanced protection. By tuning threat policies, mail flow rules, and other settings, administrators can significantly harden their organization’s email security.
Using Microsoft Secure Score and Addressing Findings
Microsoft Secure Score is a security analytics tool that measures your organization’s security posture and provides recommended actions to improve it. In the context of Exchange Online, Secure Score might flag things like unconfigured anti-phishing measures, users with external forwarding enabled, or inactive mailboxes that could be abused.
A higher Secure Score indicates that you have taken more of the recommended security actions. It’s important to regularly review Secure Score findings, because they help identify gaps in your configuration that you might have overlooked.
For example, Secure Score might recommend enabling MFA for all users or disabling auto-forwarding — steps that directly reduce risk but may require cross-team coordination to implement
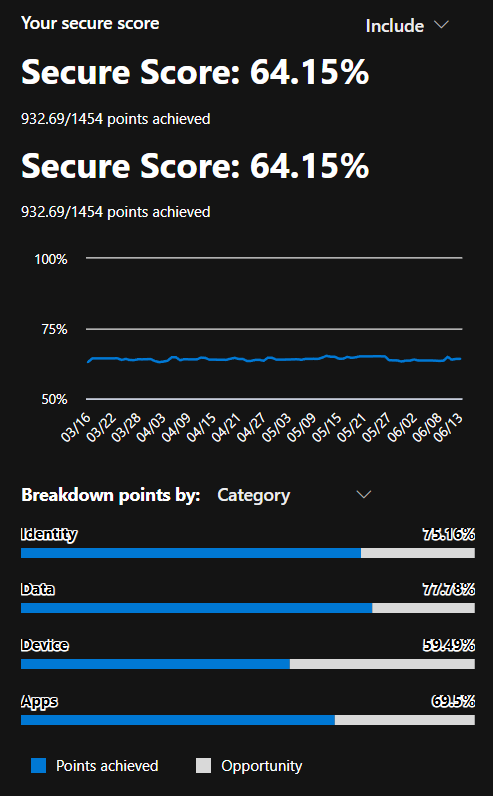
When addressing Secure Score findings, prioritize the recommendations that have high impact on reducing risk and low impact on business processes. Keep in mind that security should be balanced with usability – not every recommendation will be suitable for every environment. For instance, Secure Score might suggest a very strict attachment blocking policy that could interfere with business if your company emails a lot of macro-enabled files. In such cases, you could choose to accept the risk of a lower score rather than disrupt operations.
The key is to use Secure Score as a guide: fix what you can, understand the risks of what you can’t, and document your decisions. By systematically working through Secure Score suggestions – such as configuring DKIM, enabling audit logging, or increasing spam detection aggressiveness – you strengthen your email security posture and address known weaknesses.
Ongoing Monitoring, User Education, and Emerging Trends
Achieving good email security is not a one-time project but an ongoing process of monitoring, training, and updating defenses. After implementing DMARC and tightening Exchange Online settings, organizations should continuously monitor their email ecosystem and keep their people educated, while staying aware of evolving threats.
Mail Reputation Monitoring and Continuous Improvement
Even with protective policies in place, it’s important to keep an eye on your organization’s email reputation. Mail reputation monitoring involves tracking metrics like your domain’s sender reputation score, bounce rates, and blocklist status to ensure your emails continue to be accepted by others.
DMARC aggregate reports are one form of reputation feedback, showing whether other mail servers are having to reject or quarantine emails from your domain (which could indicate either attempted spoofing or an authentication issue on your side). By regularly reviewing such reports and using sender reputation services, you can catch problems early – for example, if a legitimate mailing campaign is mistakenly triggering spam flags or if someone is abusing your domain name.
One challenge with mail reputation monitoring is the sheer volume and complexity of data. DMARC reports are XML files that can be hard to read without parsing tools, and reputation scores from different providers can be inconsistent. To overcome this, organizations can use specialized DMARC report analysis tools or services that present the data in dashboards, like DMARC Advisor.
Maintaining a strong sender reputation requires compliance with best practices – sending only to opt-in recipients, preventing spam from your network, and promptly fixing authentication issues. The reward is better deliverability and a lower chance of your domain being untrusted by others. Regularly auditing your email configuration (SPF/DKIM/DMARC alignment, open relays, etc.) and staying responsive to Secure Score or threat alerts will ensure your email security remains robust over time.
Educating Employees and Fostering a Security-Aware Culture
While technical controls are crucial, employees themselves are a critical line of defense against email threats. Many phishing attacks succeed because an employee falls for a lure. Therefore, ongoing security awareness training is vital.
Teach staff how to recognize suspicious emails – e.g. checking for subtle sender address differences, not clicking unexpected links, and being cautious with attachments. Promote a policy of “think before you click” and make it easy for users to report potential phishing emails (Microsoft 365’s built-in Report Phishing button can be used for this).
Regular phishing simulation exercises can greatly improve vigilance. In fact, studies have shown that well-trained users are far less likely to fall for phishing attempts; around 80% of organizations report that phishing awareness training reduced the risk of employees being tricked, cutting successful phishing incidents by up to 60%.
Empower your communications and marketing teams, who often manage outbound email campaigns, with knowledge about email authentication and sending best practices – for instance, they should be aware of DMARC and why certain emails might get rejected if not sent from authorized systems.
It’s also important to establish clear processes for people to follow if they suspect an email is malicious (e.g. whom to alert, and assurance that no one will be penalized for reporting a false alarm). By making email security a shared responsibility, with leadership backing, you create a human firewall to complement your technical defenses. Remember, even the best technology can be undermined by a momentary lapse in judgment by a user – so investing in user education and a culture of skepticism toward unexpected emails is an investment in your overall security.
Looking Ahead: Email Security Trends
The email threat landscape is continually evolving. Attackers are adopting new techniques, and defenders are rising to the challenge with innovative strategies. One notable trend is the use of AI (Artificial Intelligence) by both sides.
On the offensive side, criminals are using AI to craft more convincing phishing messages (even deepfake audio/video in some cases) and to automate target research. We’re seeing early instances of deepfake-enabled impersonation scams and more refined social engineering that’s harder to detect.
On the defensive side, email security solutions are increasingly incorporating AI and machine learning to detect anomalous email behaviors and to identify threats that signature-based scanners might miss. Another trend is a move toward Zero Trust Email Security – applying the zero-trust philosophy to email by rigorously verifying sender identities, analyzing content in a sandbox before delivery, and not automatically trusting internal email either.
Additionally, standards and policies around email authentication continue to advance. Broad adoption of DMARC is growing, and with it comes the rise of BIMI (Brand Indicators for Message Identification), which rewards domains with strong authentication by displaying their brand logos in recipients’ inboxes. This not only boosts brand visibility but also gives organizations more incentive to implement DMARC at enforcement level.
Industry regulations are also pushing for stronger email security (for example, some jurisdictions mandate DMARC for certain sectors). Finally, integrated security platforms are trending – organizations are looking for solutions that combine email security with their broader security ecosystem (such as XDR – Extended Detection and Response platforms that correlate email threats with endpoint and cloud telemetry).
Staying informed about these trends will help your organization anticipate and adapt to new threats. Make sure to periodically revisit your email security posture in light of emerging attack techniques and available new features or tools from your email provider. What works today might need an update tomorrow as attackers find new gaps.
Conclusion
Email security and domain reputation management are critical components of an organization’s overall cybersecurity strategy. By implementing DMARC, you take control of your domain’s identity in emails—preventing cybercriminals from exploiting your brand and ensuring that your messages reach their intended audience securely.
At the same time, leveraging Exchange Online’s robust security features creates multiple layers of defense that filter out threats and enforce your security requirements. Equally important is the human element: continuous monitoring and user education help maintain vigilance and quickly adapt to new challenges.
In summary, a holistic approach that combines DMARC for outbound authentication, Exchange Online’s inbound and internal protections, and educated users will dramatically improve your organization’s resilience against email-based attacks. With careful planning and adherence to best practices, you can safeguard your mail flow end-to-end: protecting your domain’s reputation, keeping malicious emails at bay, and enabling your business to communicate with confidence and trust.
Need help?
When you want to optimally offer the wide range of IT environment opportunities to your organization’s business and employees in a controlled, secure and cost-effective manner, and develop know-how in your organization, we are your partner. For example; with DMARC Advisor, Sulava has secured dozens of organisations with a successful DMARC implementation.
Microsoft 365 customers have the best chance of ensuring the safe management of Azure, endpoint security, end-user identities and the safe use of M365 services and other enterprise applications.
Read more about our services and start leveraging the security of the cloud in your environment!
